A widespread “hack for hire” team that has infiltrated energy industry targets has been exposed.
The Dark Basin team, which has been linked to India’s BellTroX InfoTech Services, has allegedly targeted a number of environmental non-profits, with a particular focus on those NGOs working on the “ExxonKnew” campaign, a report from Toronto’s Citizen Lab has said.
The NGOs were pursuing a legal case against ExxonMobil in the US courts on the grounds that the company knew the risks of climate change but did nothing to prevent this occurring. A court case in December 2019 cleared ExxonMobil of claims that it had misled shareholders on climate change.
Targets of the hack linked to the ExxonKnew campaign included the Rockefeller Family Fund, Climate Investigations Center, Greenpeace, Center for International Environmental Law, Oil Change International, M+R Strategic Services, 350.org and others.
Citizen Lab has not named ExxonMobil as being behind the hack. The US company said it had “no knowledge or involvement” in the case.
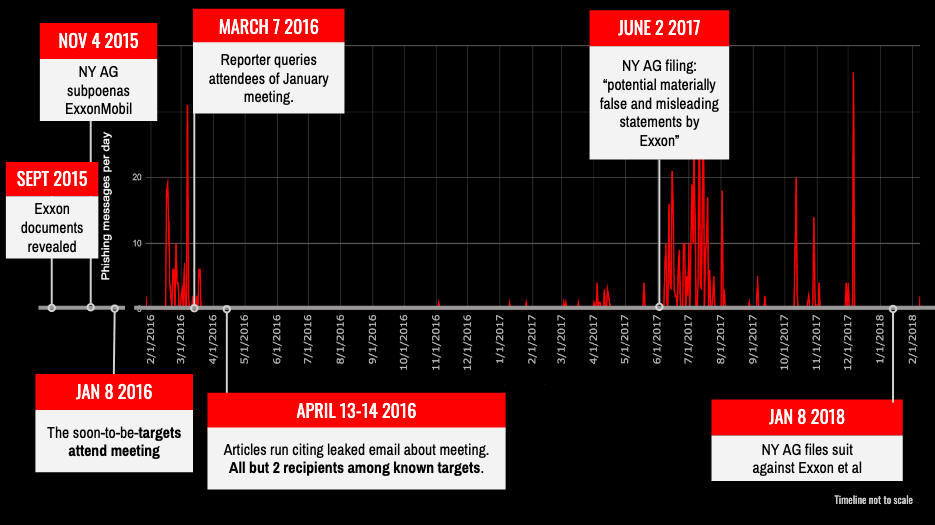
The timing of the hacks coincided with “key events” in the advocacy campaign, Citizen Lab said. An email was leaked in January 2016, which may have been hacked, followed by peaks in June 2017 and January 2018. These came as New York alleged that ExxonMobil may have made “false and misleading statements” and a lawsuit respectively.
The report noted Dark Basin seemed well informed on their targets, in one case using a child as a target of its phishing. The operators of the hacking campaign “were likely provided with detailed instructions not only about whom to target, but what kinds of messages specific targets might be responsive to”.
Citizen Lab said it would be hard to pinpoint who had commissioned such work. The report said that with many of the targets there was a “strong but unconfirmed sense that the targeting is linked to a dispute or conflict with a particular party whom they know”, but that it would be “difficult for most individuals to determine with certainty who undertakes these phishing campaigns and/or who may be contracting for such services”.
Other targets of Dark Basin included oil companies, from lawyers and staff to CEOs. The Citizen Lab report said that in some instances companies in a particular country had been targeted, ranging from service companies and energy to industry figures and government officials.
Furthermore, the hack also included lawyers in jurisdictions around the world, including the US and UK, with a particular focus on corporate litigation and financial services. Private equity group KKR and investigative short seller Muddy Waters were also targeted, as were a number of journalists.
“Hack-for-hire groups are the world’s digital mercenaries. They are focused on making money, digital warriors for hire.”
“Generally, they don’t have rules and will work for the highest dollar. These groups will sell any of their digital skill sets for those willing to pay,” said Nuspire security analyst Josh Smith.
NortonLifeLock co-operated with Citizen Lab on the report, with the technology company referring to Dark Basin as Mercenary.Amanda. Norton found that 55% of attacks were carried out in the US.
“If an email raises any red flags or just doesn’t seem right, do not click on a link, open an attachment or respond to the email,” said Nuspire’s Smith.
“Instead, forward the email to the IT department and delete it from the device. When it comes to phishing threats, a healthy dose of scepticism can go a long way.”
Updated at 6:41 pm on June 11 with comments from Nuspire’s Josh Smith.
