
The latest Searchlight Cyber threat intelligence report exposes how cybercriminals sell initial access to energy industry companies on dark web forums – with real examples of posts auctioning vulnerabilities in organisations around the world.
New energy industry report
Searchlight Cyber’s recent survey of CISOs found that 72% of oil and gas companies are already gathering data from the dark web. While that is a promising start, Searchlight Cyber noted at the time that this is less adoption than in comparable high-risk industries, see below:
- financial services (85%)
- manufacturing (83%)
- transportation (81%)
Even more concerningly, more than a quarter (27%) of energy industry CISOs said that they believe that activity on the dark web has no impact on their company.
The Searchlight Cyber report, Dark Web Threats Against the Energy Industry, demonstrates conclusively that that is not the case by showing that energy companies are routinely discussed on dark web forums. In particular, by threat actors auctioning initial access to remote software, VPNs and stolen credentials.
This analysis is based on a sample gathered over a 12-month period (February 2022-February 2023) that is indicative of the types of threat actor activity that takes place on dark web sites, forums and marketplaces.
Key findings of the report
The primary takeaway of this threat intelligence is that the predominant activity we observe against the energy industry is “auctions” for initial access to corporate networks that routinely take place on popular dark web hacking forums, including Exploit and (the now defunct) RaidForums and BreachForums.
The sample in this report alone includes numerous listings for organisations in countries all over the world, including targets in the USA, Canada, UK, France, Italy and Indonesia.
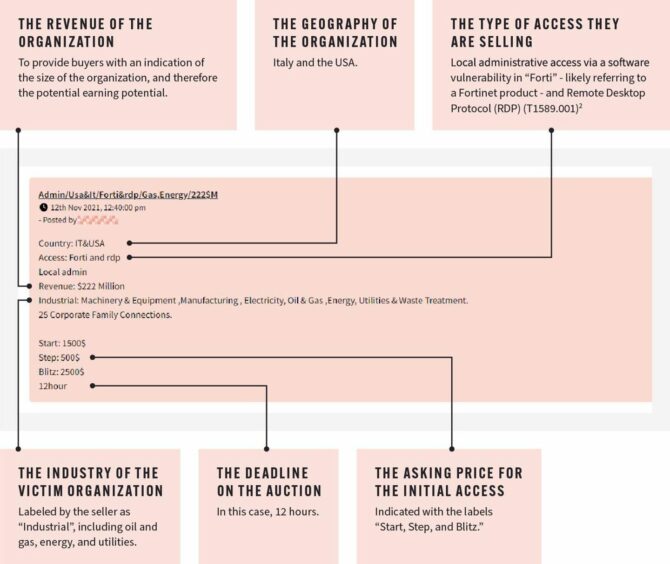
These dark web auction posts have their own standard “format”. Threat actors often use the terms “Start”, “Step” and “Blitz”, which indicate the start price, the increments of the bids, and a “buy it-now” price (blitz).
Most of these auction posts also list the access type along with the country of the organisation, its industry and its revenue. In some cases, the name of the organisation is also given.
The post in the image below is a typical example of the format and content of these posts. From the information provided by the threat actor we can determine:
While cybercriminals share this information with the intention of attracting buyers, visibility into auction activity on dark web forums offers security professionals a valuable opportunity to identify if their organisation is being targeted.
With information on the revenue, location, and technology of the potential victim, security teams can determine if they fit the profile and take mitigative action.
Even if they don’t fit the exact profile of the victim, they know this is a tactic being used against other energy companies that they should factor into their threat modelling.
Threat modelling for the energy industry
While one objective of this report was to demonstrate beyond a doubt that the activity on the dark web does impact energy companies, the second – and more important objective – was to provide security teams at energy companies with advice and guidance on what they can do about it.
Searchlight Cyber has therefore combined the reconnaissance it has observed over the past year with insight into how energy companies can start threat modelling – a process for identifying, enumerating, and prioritizing threats – based on dark web intelligence.
Where applicable, it has also provided the MITRE ATT&CK codes for the attack techniques it has observed, to demonstrate how this intelligence can practically be used by energy organisations to improve their understanding of – and defences against – threat actors that are targeting them on the dark web.
By building threat models, and feeding them with intelligence gathered from the dark web, energy organisations can identify threats against their organisations from right at the beginning of the Cyber Kill Chain, which allows their security posture to be much more responsive to emerging attacks.
Download Searchlight Cyber’s report – Dark Web Threats Against the Energy Industry – for the full analysis and findings of its dark web intelligence. For more on Searchlight Cyber, visit its website.
 © Supplied by Searchlight Cyber
© Supplied by Searchlight Cyber